Connecting to Sisense for Cloud Data Teams
To get started with Sisense, first fill out the Connect Form to establish an account within the Sisense platform. Once a successful connection is established, this form is the first step to making the account accessible.
Note: Fill out the form once to establish an account. Additional databases can be added through database settings once logged in.
General Steps to Take Before Connecting
- Ensure that the database is publicly addressable and currently up & running. If this is not the case, then a connection via SSH may be required. The documentation page on setting up an SSH tunnel breaks down the steps to help get connected to private databases.
- Verify that the database is not hosted on a local machine. Sisense for Cloud Data Teams cannot connect to databases hosted on local machines (e.g. laptops, PCs, etc.).
- Ensure that Sisense supports the database type attempting to be connected. A list of supported integrations is available here.
Successful Connection Requirements
A successful connection to Sisense can be done in a few steps:
- Whitelisting IPs - Allowing Sisense IPs into the server that the database is hosted on.
- Granting Permissions to Tables - Allowing the user that Sisense is acting as to query from tables in the database.
Instructions by Database
<a name="Whitelist"></a>
1. Whitelisting IPs
Whitelisting IPs is the process to allow Sisense for Cloud Data Team's two IP addresses (107.23.195.228 and 54.236.224.46) to pass through the firewall of the server where the database is hosted. As long as the database is hosted on a publicly accessible server, or a privately accessible server that can be accessed using an SSH tunnel, Sisense will be able to connect with this server. Please find below some sample server host types and whitelisting can be achieved.
Company Server
If the database is hosted on the Company's server, check to see if this server is publicly accessible by the internet. If not, check with the IT department on how to whitelist IPs on the Company's firewall. In some cases, an SSH tunnel will be required if the database is hosted on an internal network such as a VPN.
<a name="AmazonAWS"></a>
Amazon AWS EC2 or RDS
When the server is hosted on Amazon AWS, but not on a VPC, the first step is to log into the AWS console as an admin. Afterwards, the database instance needs to be set as publicly accessible. A Security Group on the EC2 or RDS client will need to be configured to accept connections from Sisense for Cloud Data Team's IPs. The IP requirement is a CIDR/IP, and thus the IPs that need to be added are 107.23.195.228/32 and 54.236.224.46/32. After configuring this Security Group, it must be applied to the instance of the database that Sisense will connect to.
If the database instance is hosted on a Virtual Private Cloud (VPC), there may be a secondary Security Group that needs to be configured at the network level to accept connections from Sisense's IP. In the case where the user only has a private IP for accessing the VPC within AWS, the user may be required to set up a SSH tunnel.
Note: Sisense for Cloud Data Teams does not support Amazon S3, as that is a cloud storage service rather than a database server.
Segment & Amplitude
Segment and Amplitude typically host databases on Amazon Redshift through AWS or on Heroku. These databases are typically publicly accessible. If not, check with respective Segment and Amplitude representatives to help with whitelisting Sisense for Cloud Data Team's IPs.
<a name="Heroku"></a>
Heroku
Heroku doesn't require whitelisting IPs as its databases are publicly addressable.
Microsoft Azure
For Azure, follow the following detailed steps to make sure that the SQL Server Database is accessible by the public Internet
- On the Azure Management Portal, click on VIRTUAL MACHINES.
- Select the virtual machine.
- Near the top of the page, select the ENDPOINTS page, and then at the bottom of the page, click ADD.
- On the Add an Endpoint to a Virtual Machine page, click Add a Stand-alone Endpoint, and then click the Next arrow to continue.
- On the Specify the details of the endpoint page, provide the name (MSSQL), public port (1433) and private port (1433).
- Click check mark to continue. The endpoint is created.
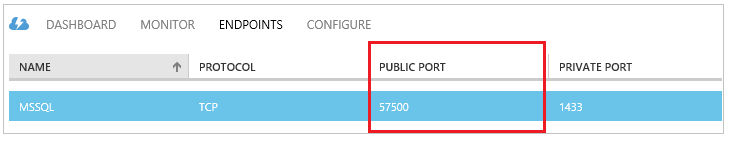
Now determine the public name of the host, called the DNS name.
- In the Azure Management Portal (or from the previous step), select VIRTUAL MACHINES.
- On the VIRTUAL MACHINE INSTANCES page, under the Quick Glance column, find and copy the DNS name for the virtual machine.
Snowflake Data Warehouse
By default, Snowflake allows users to connect to the service from any computer or device IP address. Connections to Snowflake data warehouses require a special encryption. As such, no IP whitelisting is necessary.
2. Granting Permissions to Tables
Depending on the set up, the user may have opted to create a new user to connect exclusively to Sisense as a security measure. Even if this special user wasn't created, the connected user must have been granted SELECT permissions on these tables in order to access certain tables in Sisense. The commands will vary slightly depending on the type of SQL database, and the examples below assume that the Sisense user has been named 'sisense''.
MySQL
GRANT SELECT ON my_database.schema_name TO 'sisense'@'%';
Redshift
GRANT USAGE ON SCHEMA public TO sisense;
GRANT SELECT ON ALL TABLES IN SCHEMA public TO sisense;
Postgres
GRANT USAGE ON SCHEMA public TO sisense;
GRANT SELECT ON ALL TABLES IN SCHEMA public TO sisense;
SQL Server
GRANT SELECT my_table TO sisense;
Snowflake
Snowflake allows granting privileges to roles rather than individual users. A role may need to be created exclusively for Sisense access as well.
GRANT ROLE sisense_role TO USER sisense;
GRANT USAGE ON DATABASE my_database TO ROLE sisense_role;
GRANT USAGE ON WAREHOUSE my_warehouse TO ROLE sisense_role;
GRANT USAGE ON SCHEMA public TO sisense_role;
GRANT SELECT ON ALL TABLES IN SCHEMA public TO sisense_role;
Athena
The Athena user requires the AmazonAthenaFullAccess policy as well as both read and write access to the S3 bucket.
