Microsoft Azure Active Directory SSO Integration
Adding Microsoft Azure Active Directory Single Sign On to a Cloud Data Teams account is done in two steps. First, create a registered application from the Microsoft Azure Portal that points to Cloud Data Teams. Second, configure Cloud Data Teams to direct users to the custom app.
⚠️ Please review the SSO Overview page before setting up Azure SSO. When performing a large-scale domain, SSO or SCIM change, please turn on Support Access prior to integrating, configuring and testing. It is recommended to coordinate with [email protected] so that they can assist.
Adding a registered application in Microsoft Azure
The administrator of the Microsoft Azure account is required to set up a a registered application for active directory in Azure. From the Azure portal, select Active Directory and then "Enterprise Applications"

Click the "New application" plus sign icon in the upper left-hand corner to add a new registered application. This will bring up a Create form.

Select "Non-gallery application" from the "Add your own app" window:
Name the application "PeriscopeData" and click 'Add'. Select "Single Sign On" in the right hand side bar:
Select "SAML-based Sign-on" in the Single Sign-on Mode drop down and enter the URLs below in the section "2. PeriscopeData Domain and URLs". The sitename part of the identifier should match the site name in the Periscope Dashboard URLs (for example: https://app.periscopedata.com/app/sitename/dashboardID/DashboardName).
- Identifier (Entity ID): https://app.periscopedata.com/sitename/sso
- Reply URL: https://app.periscopedata.com/auth/saml/callback
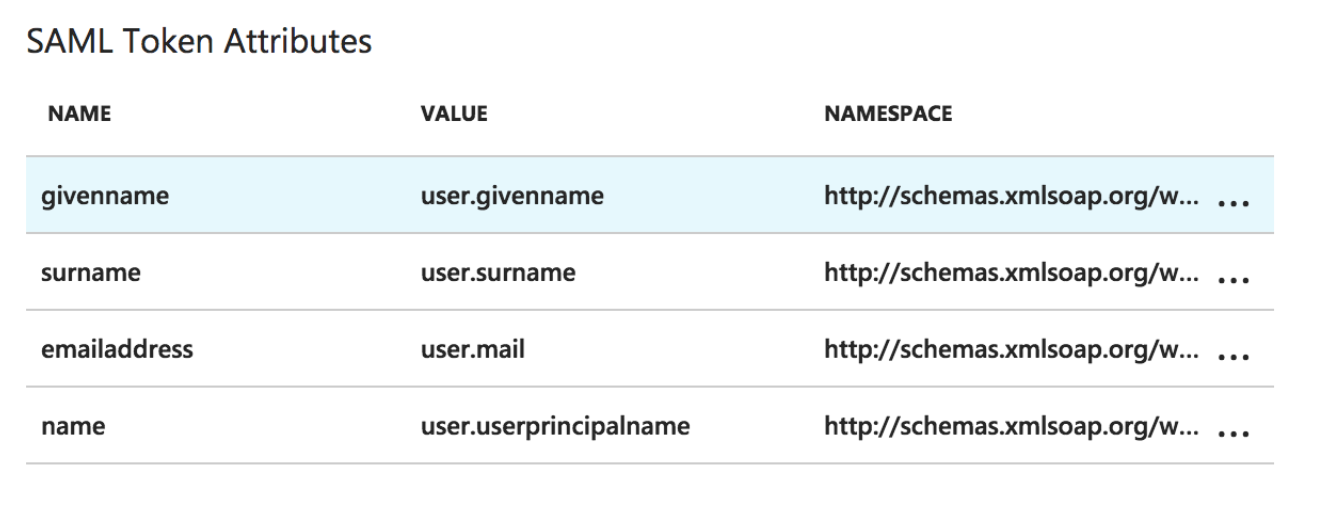
Under the section "3. User Attributes" select the check box "View and edit all other user attributes". Validate the following four attributes are configured and all values for the Namespace column match this URL: "http://schemas.xmlsoap.org/ws/2005/05/identity/claims"
In Periscope Data, open the gear menu in the bottom left and open the Billing & Security menu. Only admins have access to these settings.
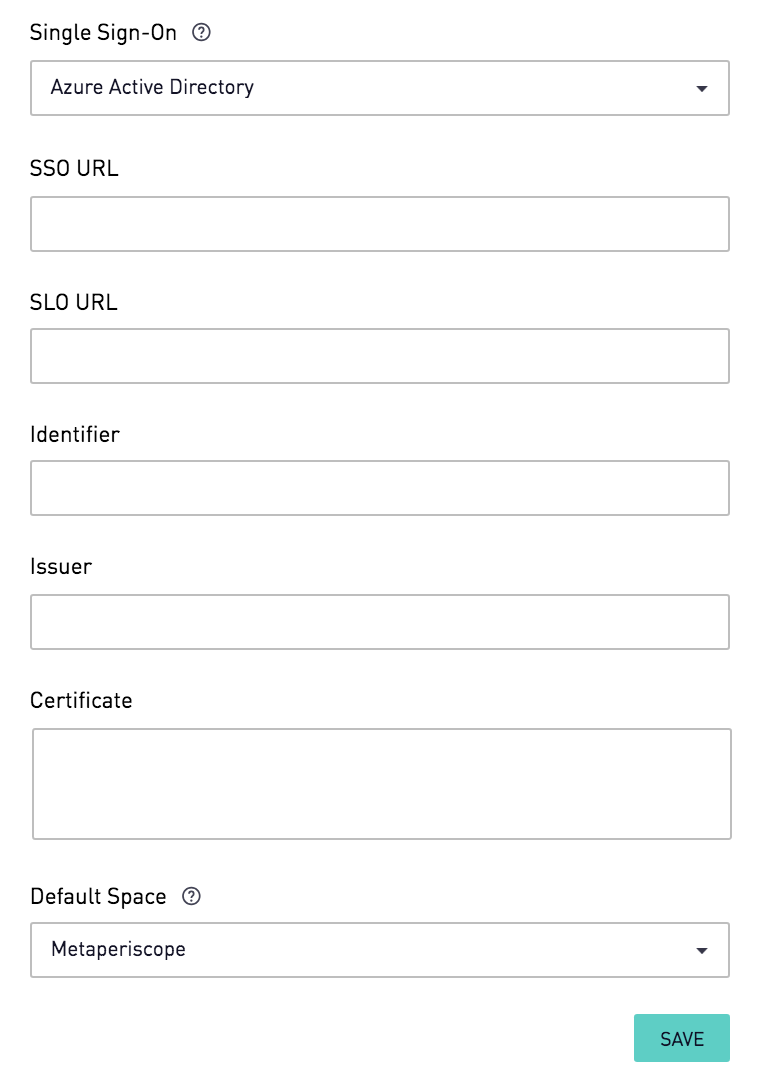
In the "Single Sign-On" section, select "Azure Active Directory". Fill in the SSO fields "SSO URL", "SLO URL", "Identifier", "Issuer", and "Certificate". To find these values in the Azure Portal, Copy the URL for the App Federation Metadata URL under the section "4. SAML Signing Certificate" and open it in a browser. This will open up an XML document.

The first tag of the XML file, note down the value for "entityID", this is the "Issuer" in the Periscope Data Form.

Find the tag "IDPSSODescriptor" with SAML protocol. Within that section, find the tag "KeyDescriptor" with use=signing. The value of X509Certificate is the "Certificate" in the Periscope Data Form.
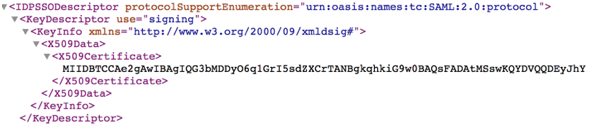
Next, find the tag "SingleSignOnService". The value for "Location" is the "SSO URL" in the Periscope Data Form.

Next, find the tag "SingleLogoutService". The value for "Location" is the "SLO URL" in the Periscope Data Form.
.png)
Last, the value for "Identifier" in the Periscope Data form should be the same URL entered for the "Identifier (Entity ID)" in the Azure section "2. PeriscopeData Domain and URLs", also noted above. These URLs should match in Periscope and in Azure.
Sites with multiple spaces can choose the default space from the "Default Space" drop down. This will be the space new users get added to when they log in to Periscope Data for the first time and are provisioned through the Active Directory Single Sign On.
Finally, click "Save" and confirm the SSO settings change by typing "Logout".

With that complete, Microsoft Azure Active Directory Single Sign On can be used to login to Periscope.
